Smart Contract Security Resources — Secureum #2
Tips, Tools & Teams
Ethereum is the most widely used smart contract platform today. Smart contracts allow permissionless development, deployment and interaction with unstoppable censorship-resistant decentralized applications (DApps) on Ethereum.
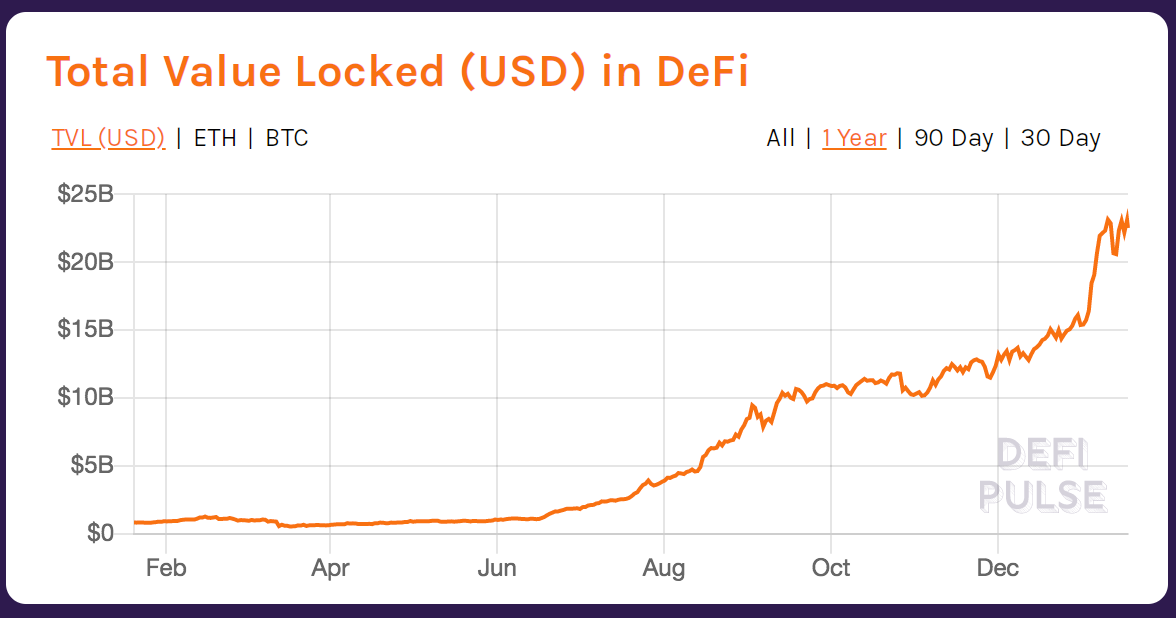
The most popular smart contract applications today are Decentralized Finance (DeFi) apps which include stablecoins, savings, trading, loans (lending/borrowing), derivatives and insurance. The Total Value Locked (TVL) across DeFi applications has grown to a staggering $20 Billion USD in the last 12 months (as shown below).
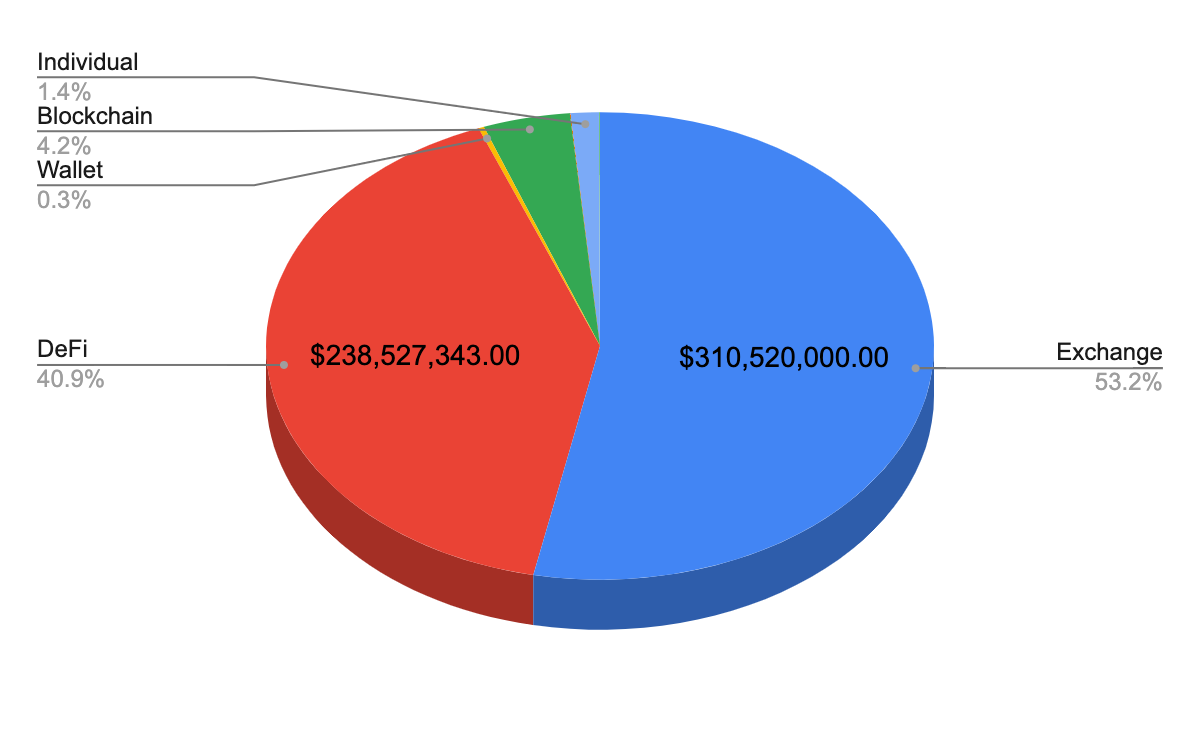
Not only has the value of tokens managed by such applications increased exponentially but also the complexity of their smart contracts has grown significantly. Simple standalone token contracts have made way for complex contract interactions with other composable contracts and oracles. This growth of value and complexity has made the security of smart contracts more critical than it has ever been. A BlockThreat study estimates that DeFi hacks amounted to a shocking $238 Million USD in 2020 which was ~40% in value of all blockchain-related incidents last year (as shown below). And these account only for the publicly disclosed high-profile incidents whereas the full impact is likely even worse.
While smart contract security has always been recognised as being extremely critical to the growth of the Ethereum ecosystem, there’s never been a greater need for increased awareness, updated resources/tools and collective wisdom to further strengthen the seat belts of Ethereum and make this fast ride towards decentralized Web3 also more secure.
As a small step in that direction, this post provides an overview of smart contract security resources by collating references to the most popular tips, tools and teams, and describing their key highlights.
Security Tips
Smart contracts for Ethereum are written in Solidity language targeting the Ethereum Virtual Machine (EVM) bytecode. Vyper language is a distant second with only a few projects such as Curve and Yearn starting to use it recently.
Security best practices and recommendations for smart contracts stem from aspects such as intricacies of Solidity language, compiler vulnerabilities, internals of EVM, invalid assumptions about randomness, about privacy, transparency and ordering of blockchain transactions and their impact on state, dependency on external contracts/libraries and oracles, lack of input validation under byzantine threat model, access control failures, reentrancy and DoS. Vulnerabilities related to contract logic are particular to the specific applications.
Language & Compiler: A good starting point is the list of Solidity-specific security pitfalls and recommendations. There is also a list of known bugs in the various compiler versions.
Solidity compiler includes an experimental formal verification tool SMTChecker which considers require/assert statements as specifications to either prove them to be true or provide counterexamples otherwise. This also checks for arithmetic underflow/overflow and unreachable code.
The language has continued to add security-specific features across the versions such as the most recently introduced default overflow/underflow checks for arithmetic operations in v0.8.0.
Ethereum Internals & Externals: Understanding security aspects of Ethereum smart contracts is incomplete without knowledge of EVM internals, workings of client implementations (e.g. Geth or OpenEthereum) and visualising the way external users interact with it by learning to navigate block explorers such as Etherscan.
Programming: Consensys Diligence has a list of patterns related to mindset philosophy, attacks, defensive programming, failure preparation and documentation.
Trail of Bits has lists of high-level recommendations, secure development workflow, token integration checklist and some examples of vulnerabilities. Another great place to learn about specific vulnerabilities is the documentation from their Slither tool’s 70+ detectors.
There have been many other efforts by individuals, community and academia to document, evaluate and classify smart contract vulnerabilities (e.g. 1, 2, 3, 4, 5, 6, 7, 8).
Public Audit Reports: A great resource to learn about real-world smart contract security is from the project audit reports published by teams specializing in this domain such as from Trail of Bits, ConsenSys Diligence, OpenZeppelin and Quantstamp. ConsenSys maintains a consolidated project-based repository here.
These reports illustrate the security issues found with associated vulnerability type/severity categorization, potential exploit scenarios and recommended fixes.
Exploit Post-mortems: Analysis of real-world exploits and root-causes of their underlying vulnerabilities is another way to learn from hindsight what went wrong in practice and what can be done better in future. Good examples of this are analyses of DAO exploit (Vitalik’s related post), Parity Multisig 1, Parity Multisig 2, Bancor, ERC20 missing return value, 0x, Livepeer, DDEX/bZx, MakerDAO, Curve, Authereum, Nexus Mutual, bZx, Lendf.Me, Argent, Balancer, Opyn, Uniswap, Lien and many others.
Security Tools
Smart contract security tools are critical in assisting smart contract developers and auditors with showcasing (potentially) exploitable vulnerabilities, highlighting dangerous programming styles or surfacing common patterns of misuse. None of these however replace the need for manual review/validation to evaluate contract-specific business logic and other complex control-flow, data-flow & value-flow aspects.
There are several tools for test coverage, linting, disassembling, visualization, static analysis, dynamic analysis and formal verification of smart contracts. Most of these are open-source but only some are actively maintained.
The Ethereum developer tool list from ConsenSys is the most comprehensive and updated resource. The Solidity compilation is another good one.
Trail of Bits
Trail of Bits has a broad suite of security tools which include:
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract details, and provides an API to easily write custom analyses. Slither enables developers to find vulnerabilities, enhance their code comprehension, and quickly prototype custom analyses. It implements 71 detectors in the publicly available free version.
Manticore is a symbolic execution tool for analysis of Ethereum smart contracts (besides Linux binaries & WASM modules). Echidna is a Haskell program designed for fuzzing/property-based testing of Ethereum smarts contracts. It uses sophisticated grammar-based fuzzing campaigns based on a contract ABI to falsify user-defined predicates or Solidity assertions.
Eth-security-toolbox is a Docker container preinstalled and preconfigured with all of Trail of Bits’ Ethereum security tools. Ethersplay is a Binary Ninja plugin which enables an EVM disassembler and related analysis tools. Pyevmasm is an assembler and disassembler library for the Ethereum Virtual Machine (EVM). Rattle is an EVM binary static analysis framework designed to work on deployed smart contracts. Ida-evm is an IDA Processor Module for the Ethereum Virtual Machine (EVM). Evm_cfg_builder is a tool used to extract a control flow graph (CFG) from EVM bytecode and used by Ethersplay, Manticore, and other tools from Trail of Bits.
Crytic-compile is a smart contract compilation library which is used in their security tools and supports Truffle, Embark, Etherscan, Brownie, Waffle, Hardhat and other development environments. Solc-select is a script to quickly switch between Solidity compiler versions. Etheno is the Ethereum testing Swiss Army knife. It’s a JSON RPC multiplexer, analysis tool wrapper, and test integration tool.
ConsenSys Diligence
ConsenSys Diligence, the security team from ConsenSys, also has a broad suite of security tools which include:
MythX is a powerful security analysis service that finds Solidity vulnerabilities in your Ethereum smart contract code during your development life cycle. It is a paid API-based service which uses several tools on the backend including a static analyzer, symbolic analyzer and a greybox fuzzer to implement a total of 46 detectors. Mythril is the open-source component of MythX.
Scribble is a verification language and runtime verification tool that translates high-level specifications into solidity code. It allows you to annotate a solidity smart contract with properties.
Karl is a monitor for smart contracts that checks for security vulnerabilities using the Mythril detection engine. It can be used to monitor the Ethereum blockchain for newly deployed vulnerable smart contracts in real-time.
Theo is an exploitation tool with a Metasploit-like interface, drops you into a Python REPL console, where you can use the available features to do smart contract reconnaissance, check the storage, run exploits or frontrun or backrun transactions targeting a specific smart contract.
Visual Auditor is a Visual Studio Code extension that provides security-aware syntax and semantic highlighting for Solidity and Vyper. Surya aids auditors in understanding and visualizing Solidity smart contracts by providing information about the contracts’ structure and generates call graphs and inheritance graphs. It also supports querying the function call graph in multiple ways to aid in the manual inspection of contracts.
OpenZeppelin
OpenZeppelin is best known for its security-focussed smart contract libraries such as those for tokens, access control, math and proxies which are used across most projects.
They recently announced the release of their OpenZeppelin Defender product which claims to be the first SecOps platform for Ethereum with three major benefits: (1) Admin: Seamlessly manage all smart contract administration including access controls, upgrades, and pausing. (2) Relay: Implement private relayers with support for testnets, mainnet, layer 2 and sidechains (3) Autotasks: Create and run scripts in a serverless environment that call your smart contracts and other web services.
Ethernaut is a Solidity-based educational game where each level is a smart contract that needs to be hacked, which can be a fun way to learn about security of Solidity and EVM.
ChainSecurity, SmartDec, RV & Others
There are many other tools such as Securify and VerX from ChainSecurity, SmartCheck from SmartDec, K-Framework (KEVM) based analysis, modelling and verification tools from Runtime Verification (RV), Certora Prover, DappHub’s Hevm and Oyente. There is a good compilation of Ethereum-related formal verification projects here.
Platforms such as Nexus Mutual and Cover allow users to buy insurance coverage on smart contract risk exposure.
Summary: Many of these tools have been built by security teams that provide smart contract security audit services while some have origins in academic research. Most are open-source and freely available but there are some accessible only behind paywalls. While this may seem like a lot of tools, it remains to be seen how many of them are kept updated as Ethereum continues to evolve rapidly with new features, Solidity updates, EVM upgrades, new languages (e.g. Vyper), Layer 2 technologies and Eth2 migration in coming years.
Security Teams
Despite launching in 2015, we are still in early phases of a Cambrian explosion of Ethereum technology today and perhaps comparable to the first few decades after the birth of Internet. As a result, most teams building Ethereum applications are also having to contribute towards building out parts of the Ethereum infrastructure themselves (i.e. apps inspiring infrastructure).
In the context of security, this involves understanding the very depths and extreme corner cases of the infrastructure with the risk of irreversible loss of funds and looming shutdown in the event of major security incidents. This has led to projects increasingly relying on external security audits/assessments as a stamp of expert approval typically justified by lack of sufficient in-house security expertise and accelerated time-to-market aspirations.
While projects with tokens, funding or revenue streams build out internal security expertise, there are numerous security individuals, teams and companies providing auditing/consulting services in this space. Some often cited names in this space are ABDK, Arcadia, Beosin, Blockchain Consilium, CertiK, ChainSafe, Chainsulting, CoinFabrik, ConsenSys Diligence, Dedaub, G0, Hacken, Haechi, Halborn, HashEx, Iosiro, Least Authority, MixBytes, NCC, NewAlchemy, OpenZeppelin, PeckShield, Pessimistic, PepperSec, Pickle, PWC Switzerland (former ChainSecurity), Quantstamp, QuillHash, Runtime Verification, Sigma Prime, SlowMist, SmartDec, Solidified, Somish, Trail of Bits and Zokyo.
Many projects also have individual bug bounty programs along with those covered by platforms such as Ethereum Foundation, Gitcoin and Immunefi.
Summary
Smart contracts are new and unique to Web3. Ethereum is the most popular smart contract platform today. As I wrote in my earlier post on Web3 security, there are ten key aspects that make Ethereum smart contract security extra challenging compared to traditional Web2 security.
This post provides a compilation of resources related to smart contract security best practices, security tools and teams providing smart contract auditing/consulting services. I’m familiar only with a few of these resources and therefore this is not an endorsement of any kind. It’s also likely that I’ve missed some resources. I plan to maintain actively updated repositories with community participation.
I hope you found this somewhat useful. Thanks for reading and look forward to your comments and feedback.


I think ConsenSys changed the URLs which mentioned in this substack!
You can reach out this links from here : https://consensys.github.io/smart-contract-best-practices/